Overview
This guide will breakdown how the SMS OTP API works and help you understand how to authenticate users.
How does SMS OTP API work?
Conceptually, SMS OTP work quite simply in 3 steps.
- Generate a pre-authenticated One Time Passcode (OTP) strongly tied to a user
- Send the user the OTP through a communication channel such as their phone.
- Verify the OTP and authenticate the user
One time passcodes in the recent years has become quite famous and now used by multiple websites as either the primary method of login or as Second factor authentication (2FA).
Here, we will explain how using SMS OTP with EZiD APIs work.
Step 1: Send SMS OTP to user
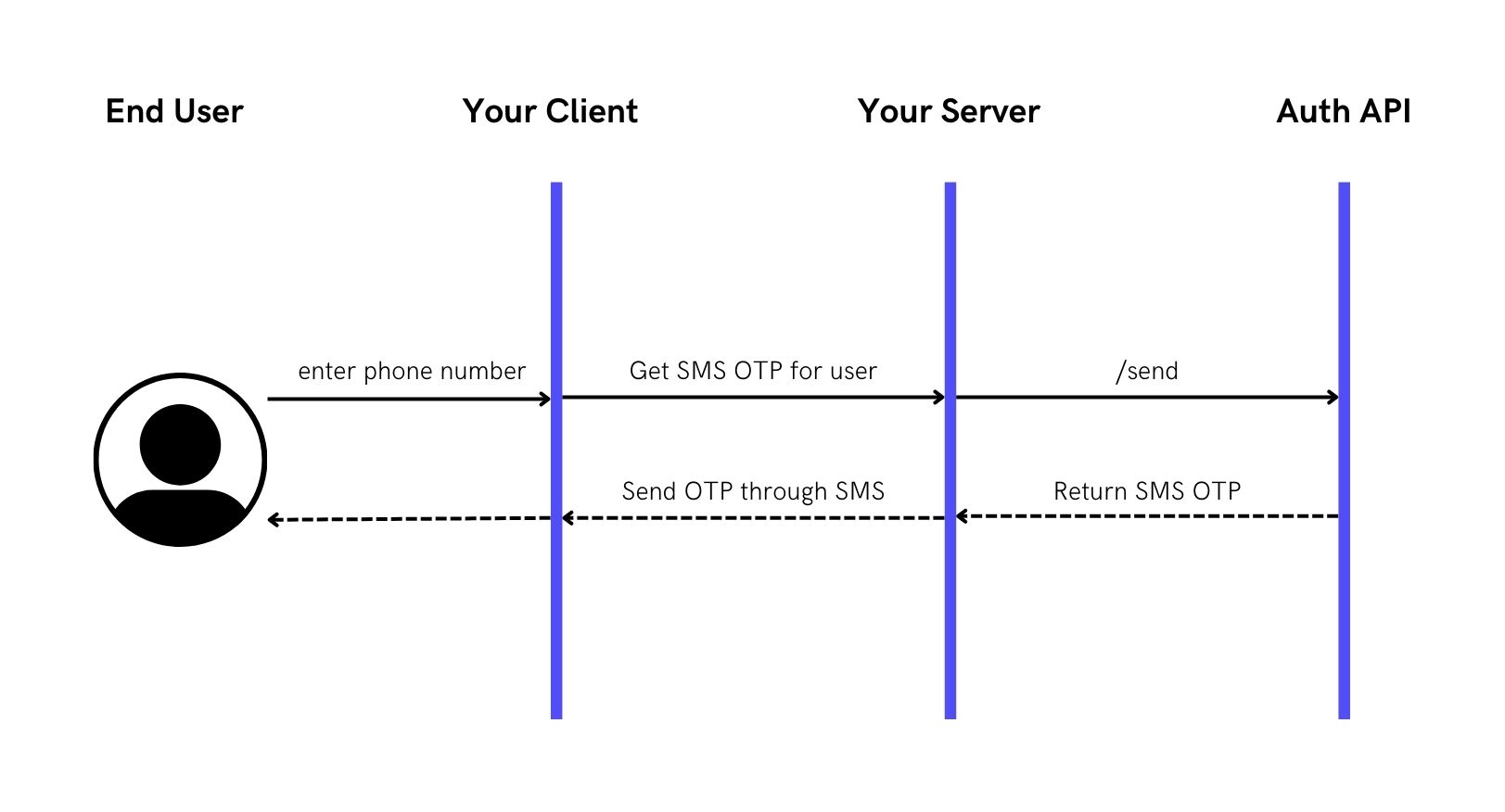
Here, we use the /send API to send an SMS to a user through their Phone with a single API. An OTP is returned in format of your choice:
Please Note: Our
/sendAPI allows you to decide the length of the OTP sent to your end user.Default value: 6 digits.
Min: 4 digits
Max: 10 digits
Once the OTP is returned to the user, the next step is to allow the user to enter the OTP on your platform and then verify if the code is correct.
Step 2: Verify SMS OTP and authenticate user
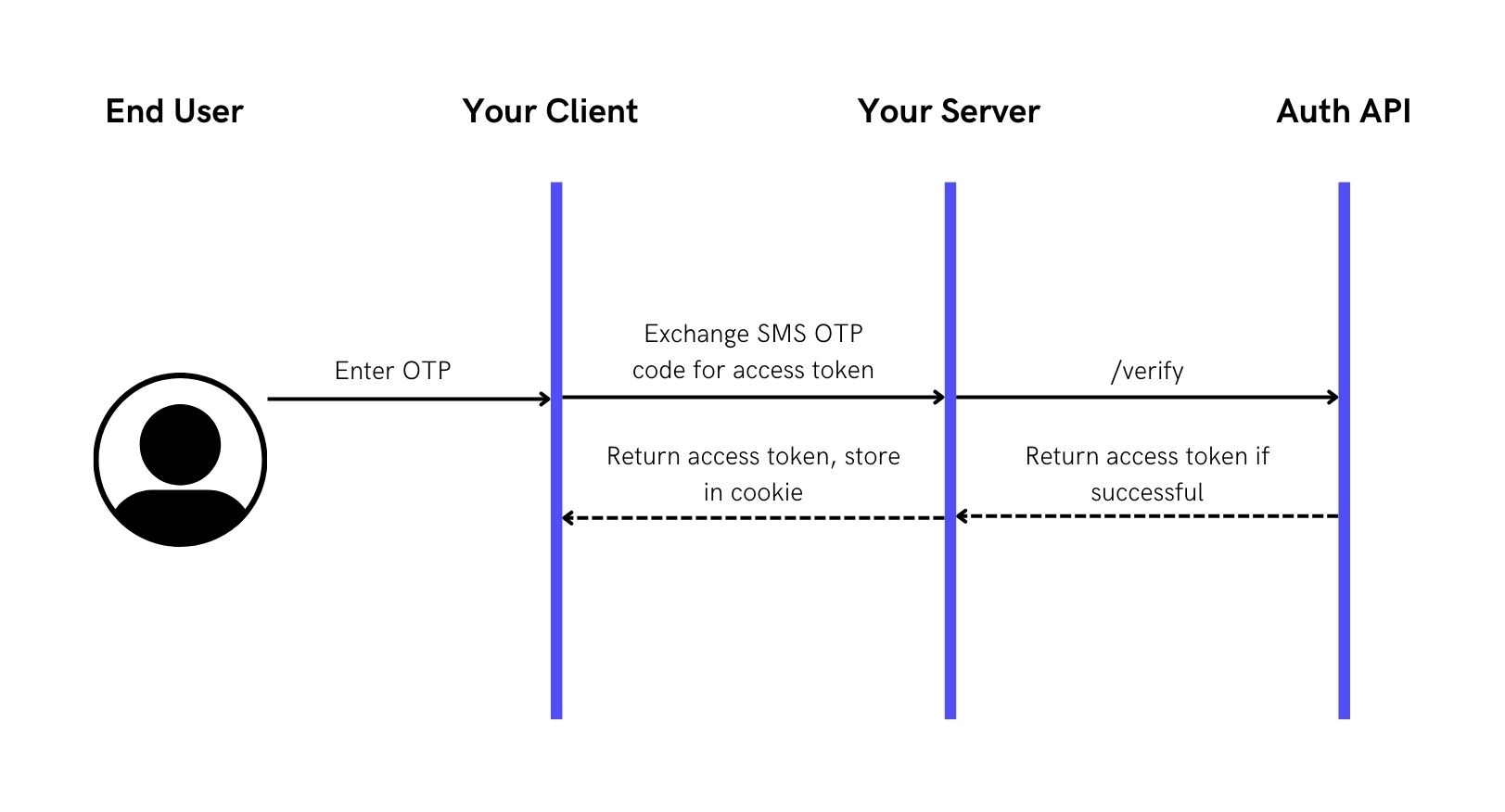
Here the API returns an access_token and an id_token
There are a few reasons as to why the access_token is not directly provided in the Magic Link:
Please Note: We also have
/generateAPI for SMS OTPs where you can choose your own provider to send the messages and use us purely for authentication. This can be found as an extra section at the bottom of the/sendAPI page.
Step 3: Use access_token from authenticated user to access app resources
access_token from authenticated user to access app resources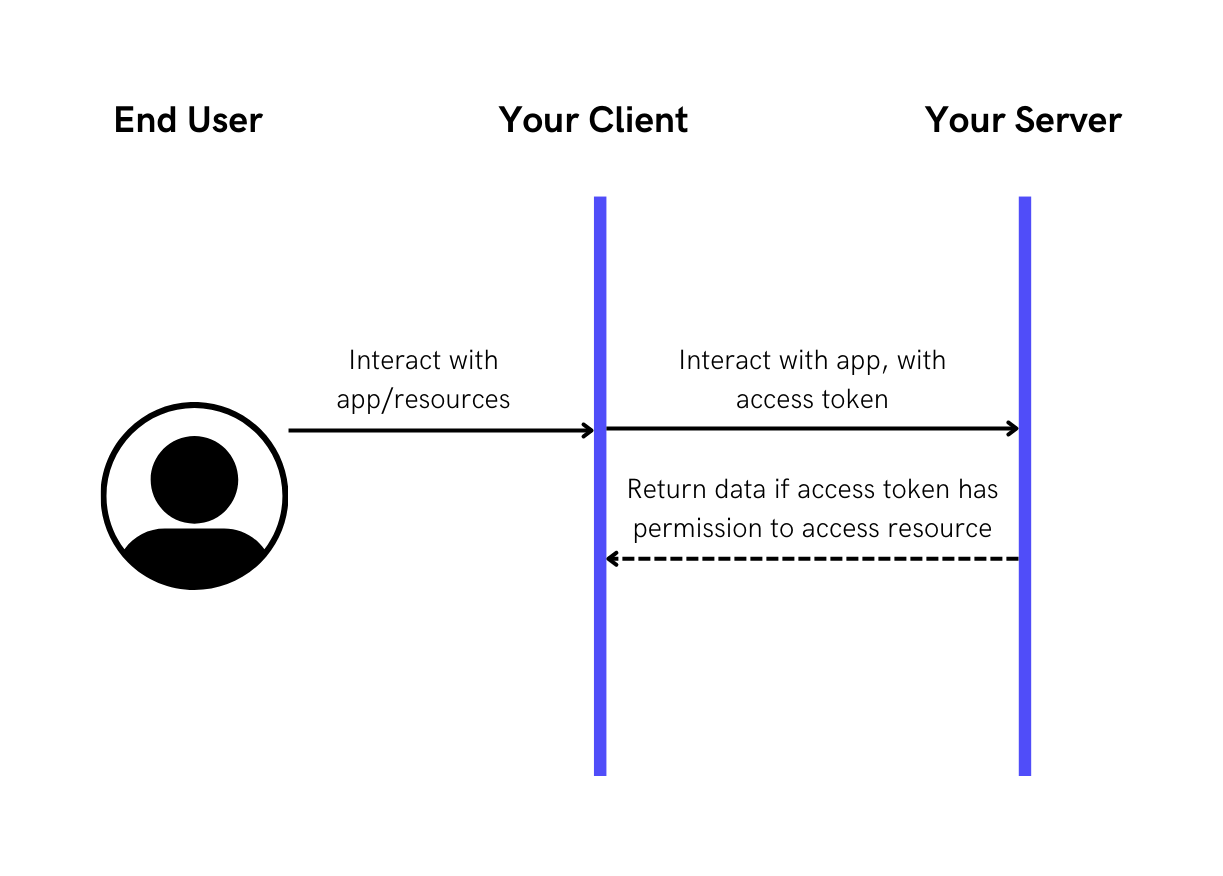
Now that your user has an access_token, they can use this to access resources as specified in claims (assertions about the user that would allow them to access parts of your application) that is now embedded with the access_token.
